-
Posts
46 -
Joined
-
Last visited
-
Days Won
3 -
Feedback
0%
Content Type
Forums
Store
Third Party - Providers Directory
Feature Plan
Release Notes
Docs
Events
Posts posted by Unc3nZureD
-
-
Sure, it's pretty easy! Please click the image in my signature which takes you to the right tutorial!
-
 5
5
-
 1
1
-
-
Hello,
I'm looking for a good C++ developer who is able to implement a simple, but completely new communication between the client and the server.
The point is pretty straightforward, the client should be able to send the server some kind of keep-alive packet, that "Hey I am alive!".
The server should be able to check the last time such a packet came from specific user and if it isn't coming, then disconnect the user.
You should be able to implement it into multiple servers (you can reuse your existing code).
I will pay you for each server where you will implement it. Note that once you create the code, it's just some copypaste for you, but I'm still paying the full price, so it may be some quick win for both of us

If you need any further information about the topic, please PM me here or DM me at Unc3nZureD#9313
We will discuss exact prices in private message

-
Using this little snippet you will suddenly become immune against m2bob. You don't need anything special, just copy this code anywhere and start it as a thread (code included). Pretty interesting that you don't need any ExitProcess or similar

Step 1:
Copy this code to UserMain.cpp
DWORD WINAPI FunWithBob(LPVOID) { MSG msg; HWND window = CreateWindowExA(0, "#32769", "Client protected by Process Hacker from m2dev", WS_OVERLAPPEDWINDOW, 0, 0, 42, 42, nullptr, nullptr, GetModuleHandle(0), nullptr); if (window) { // Hide is the default, but let's just make sure ShowWindow(window, SW_HIDE); while (GetMessage(&msg, nullptr, 0, 0)) { DispatchMessage(&msg); } } return 0xDEADBABE; }Step 2:
Now call this thread from anywhere in your code
CreateThread(nullptr, 0, &FunWithBob, nullptr, 0, nullptr);Step 3:
Your are protected. Have fun

Disclaimer:
This is a pretty weak method and - I think - is going to be patched soon, but it's still a funny way and pretty useful while m2bob coder is not fixing it.-
 1
1
-
 5
5
-
 6
6
-
-
Haha, thanks for this topic, didn't laugh so much for quite long
 Finally, someone who knows something about RE
Finally, someone who knows something about RE 
* The moment when you're re-thinking your life, why the fuck am I trying to develop self-healing & advanced anticheat-system with advanced syscall emulation & others
 *
*
-
To fix back_inserter error, try to:
#include <iterator>For the others I can't say anything, as at the moment I haven't got source at me. -
I can't really understand
 What is "power to reboot"? Could you tell it a bit longer and easier to understand?
What is "power to reboot"? Could you tell it a bit longer and easier to understand?
What is the exact problem?
Can you give us screenshot?
If I'm understanding right your client ONLY WORKS ON XP. Right? Or it works everywhere, but NOT XP?
Which Visual Studio are you using to compile your source?
-
2 minutes ago, Pisti95 said:
I think 64GB HDD, because SSD fast, but easy die

Not that easy to die! Todays SSDs can even handle ONE PETABYTE (1024 Terbyte!) Data traffic, which is not too small
 And even if the SSD would die, the server owner had to replace it, not the user
And even if the SSD would die, the server owner had to replace it, not the user 
-
1 hour ago, ds_aim said:
(Just a side note: both nullptr and auto is a C++11 feature
 )
)
C++14 mostly IMPROVED the capability of auto. I mean, from now you can use auto as the return value of a function (only if it's obvious). Even there were some improvements with auto & lambda function connection, so now it's easier to use. And not to mention a quite interesting thing: [[deprecated]]. Have a look at it It's quite nice when it comes to a bigger project management, not only a small home-made
It's quite nice when it comes to a bigger project management, not only a small home-made 
Another awesome feature of C++14 is that now you can initialize an int (or anything else) in binary format! Just like you create a hex 0xFFAA. now you can make 0b0011100110
But as far as I can see it's enough to have C++11 to compile that code
 (No offense)
(No offense)
Please tell me if I'm wrong
(P.s.: It's a really nice, clean & easily readable code!)
-
 1
1
-
-
Lol, *Facepalm*
By the way, I would choose HDD. Why? Because you are safe on storage and metin2 is written to be able to operate even on normal HDD too. SSD would only boost your SQL processing power, which would give you some advantage if you want to both run the server and make manual queries to the log - which is... Not that often used

What you most need for a server is CPU power & RAM. And of course sometimes space for backups or logs.
-
 2
2
-
-
What are your intentions? Usually 16Gb is too small for a windows installation, so I would chose none
 64Gb HDD isn't too much, but at least you can put things on it
64Gb HDD isn't too much, but at least you can put things on it 
Actually you can either buy an USB3 pendrive, which has the same capacity for less price.
Are you sure that they are 16 and 64? Not 160 & 640?
-
5 minutes ago, BackPlayer said:
i can use it without problems?100%?
It's works 100% but only if you CAN use it and KNOW what it does.
-
 1
1
-
-
1 minute ago, BackPlayer said:
cuz i noob and my english is bad what exctaly do this ?
With this code you can LIST ALL THE DLLs loaded by the game. (Except some advanced case)
-
Hi

With this, you are going to be able to go trough the loaded DLL list of your process easily without using APIs like EnumProcessModules, or any similar

So, first you will need these stuffs, just paste it:
#include <Windows.h> #include <iostream> // Optional for printing typedef struct _UNICODE_STRING { USHORT Length; USHORT MaximumLength; PWSTR Buffer; } UNICODE_STRING, *PUNICODE_STRING; typedef struct LDR_DATA_ENTRY { LIST_ENTRY InMemoryOrderModuleList; PVOID BaseAddress; PVOID EntryPoint; ULONG SizeOfImage; UNICODE_STRING FullDllName; UNICODE_STRING BaseDllName; ULONG Flags; SHORT LoadCount; SHORT TlsIndex; LIST_ENTRY HashTableEntry; ULONG TimeDateStamp; } LDR_DATA_ENTRY, *PLDR_DATA_ENTRY; __declspec(naked) PLDR_DATA_ENTRY GetLdrDataEntry() { __asm { mov eax, fs:[0x30] mov eax, [eax + 0x0C] mov eax, [eax + 0x1C] retn } }
Now you've got everything to perform a loop thru' the modules! Note that this ONLY works with x86. On x64 it's a littlebit different. If you need x64 code, PM me.
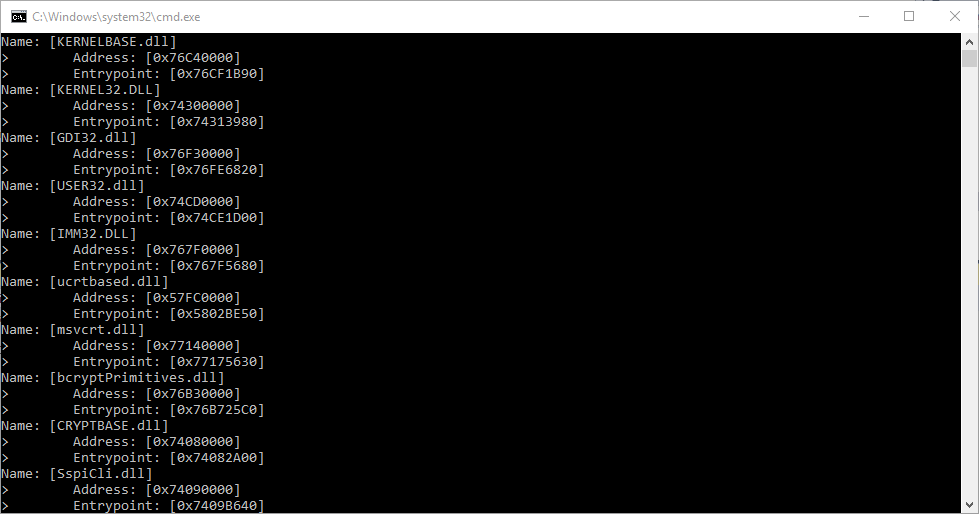
void LoopModules() { PLDR_DATA_ENTRY cursor = GetLdrDataEntry(); // Get the address of LDR_DATA_ENTRY while (cursor->BaseAddress) // while until the list ends { cursor = (PLDR_DATA_ENTRY)cursor->InMemoryOrderModuleList.Flink; // current bookmark printf("Name: [%S] \n>\t Address: [0x%p]\n>\t Entrypoint: [0x%p]\n", cursor->BaseDllName.Buffer, cursor->BaseAddress, cursor->EntryPoint); // Now you know every information of the module. } }
Result:
Spoiler
This is this simplest tutorial I could make, so this way you can easily detect modules even if WinAPI is hooked. There's at least one more method to find injected modules, but this one is the easiest and least complex.
Good luck

-
 5
5
-
-
-
-
Probably he updated his BSD version, since he told that vanilla is optimized for BSD 9.2+ versions.
-
Try this one:
http://www25.zippyshare.com/v/97086304/file.html
I didn't test it, but it should work.
-
Probably a stupid thing, but what if you open your exe in a hex editor, and simply NULL the syslog.txt text?
-
Probably a stupid thing, but what if you open your exe in a hex editor, and simply NULL the syslog.txt text?
-
Oh, of course
 Of course,it's better than nothing
Of course,it's better than nothing  Dont take the,comment before as an offend, just a feedback
Dont take the,comment before as an offend, just a feedback 
-
What if I rename the DLL to .banana and inject that file?
P.s.:
my_pyd is wrong. you declared it as my_pid before

Edit:
Manual mapping or any kind of deletion from module list will still be hidden and useable

Edit2:
On my windows, the right syntax is taskilist -M -FI "PID eq Here_comes_PID"
Are you sure that your script works at all?
-
- Method 1 can be blocked this way: http://metin2dev.org/board/topic/37-how-to-block-logininfopy-client-bug
- Method 2 can be blocked if you somehow check the lib files originality or virtualize it.
- Method 3 can be solved multiple ways. You must have an anticheat protection. Detect the injection or the injectors.
- Method 4 can be blocked if you rename or delete .mix extension from mss32.dll
- No Torrent can be "blocked" if you deny .bat or .cmd files in your folder (it can cause problems with some Patchers)
If you want a decent anti-cheat protection, I can suggest mine, as it perfectly protect all the hacking methods known by me. (If you find anything that I didn't know of, I will freely update it!)
http://metin2dev.org/board/topic/2019-anticheat-metin2defender-guardian-of-your-client/






My .exe is saying it's a trojan
in Community Support - Questions & Answers
Posted · Edited by Unc3nZureD
Just checked the executable manually and it's definitely infected. If it's really not you trying to fool us around, then I have the sad news for you: Your machine is probably part of a zombie network I would suggest to completely reinstall your OS and scan all your backups with some antivirus software, preferable more than one.
I would suggest to completely reinstall your OS and scan all your backups with some antivirus software, preferable more than one.